The Xentara Security Model
It’s a wired world, with the Industrial Internet of Things (IIoT) and Manufacturing X demanding network connectivity from nearly every system. That’s why Xentara uses a multi-mesh security approach to keep your data safe from any attackers.
Keep Your Data Safe and Secure

You want to be sure who can access your data – and who can’t. That’s why Xentara features extremely fine grained access controls.
Access rights can be assigned to any part of the System Model – whether it’s a single data point, a data group, a devices, or an entire bus.


Encrypt Your Connections

Xentara uses secure communications protocols where possible. Usually, this involes the use of encryted Transport Layer Security (TLS) connections from and to other systems. TLS is the standard security protocol used by most secure communication protocols, like SSH and HTTPs.
In the case of third party protocols, Xentara always strives to default to the highest security and encryption level offered by the protocol.
Manage Your Users

Xentara comes with advanced user and rights management functions.
Developers and administrators can assign rights to individual users or create roles with different access levels and assign them to users as needed.
A hierarchy of roles allows inheriting permissions.

Authenticate Your Way

Xentara uses multi-mesh authentication, allowing multiple different ways of authenticating remote clients. The following remote authentication methods are supported by Xentara:
- OAuth 2.0
- Certificate based
- Username / Password
Which authentication methods are supported by a specific remote access service depends on the protocol used.
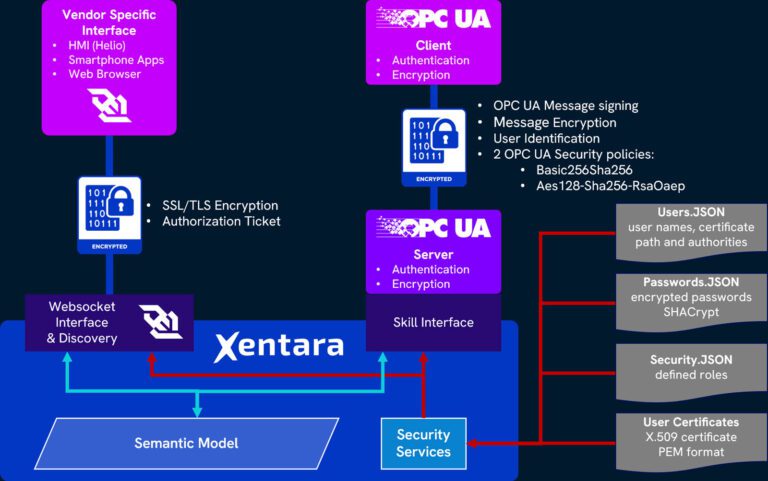
Nerd Stuff: Multi-Mesh Security
In this image, you can see an example of our multi-pronged security approach in action.
The Xentara Security Services have authority over all incoming or outgoing connections, irrespective of type. Here, a websocket connection to a vendor specific web app is encrypted using SSL/TLS while the OPC UA Server automatically defaults to its protocol’s native encryption.
Users can authenticate via password or certificate, and the access rights are defined in user roles.